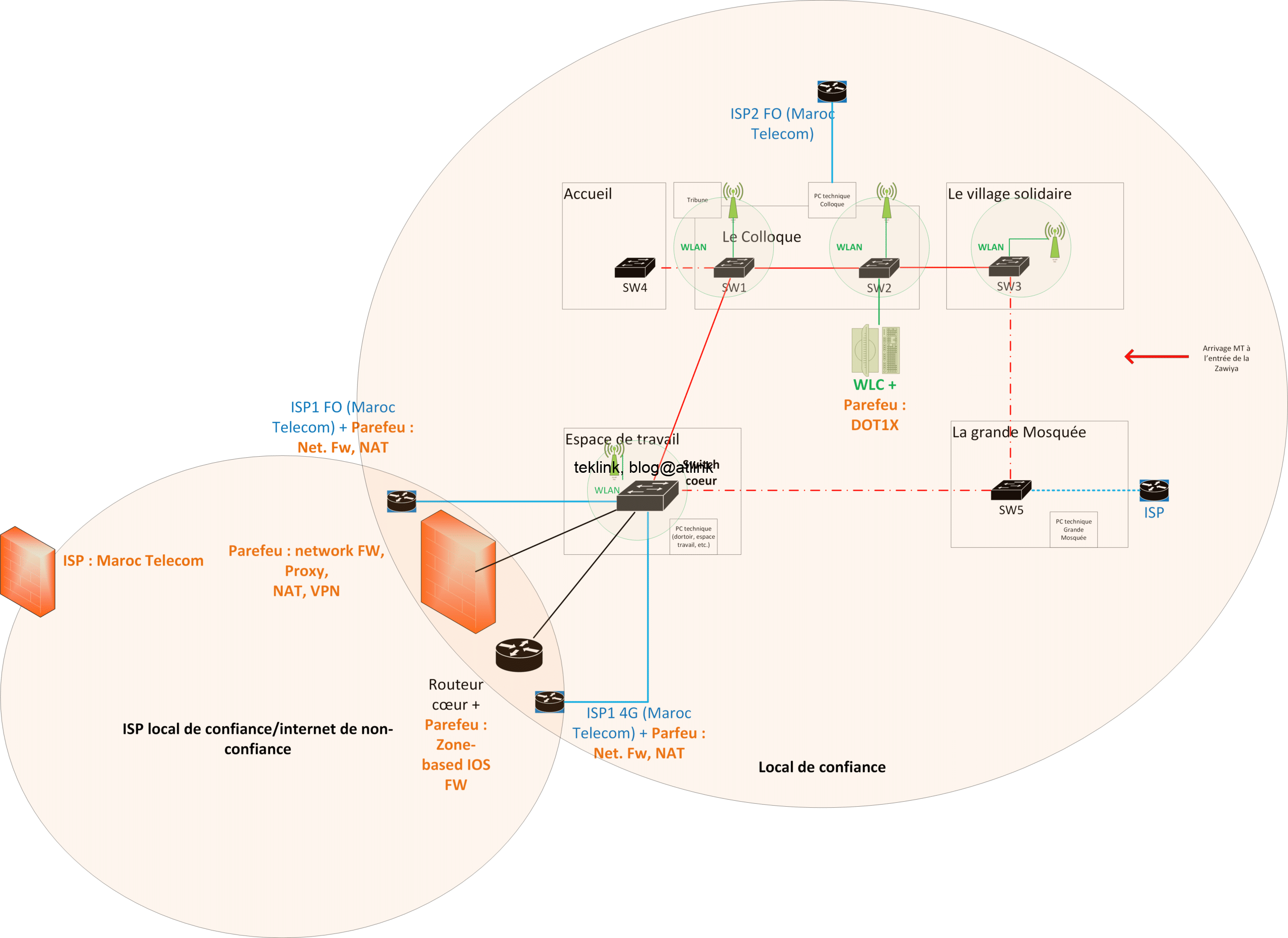
Protected: An Example Network From Scratch… Build your Network Security
There is no excerpt because this is a protected post.

There is no excerpt because this is a protected post.
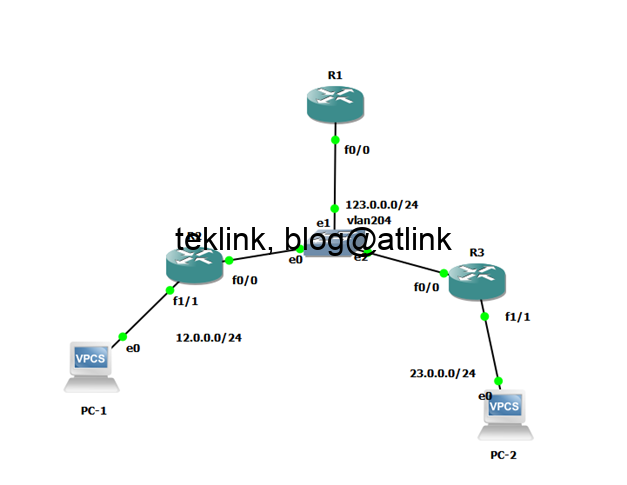
In this blog, we discuss when a gateway decides that it’s not a good gateway any more and proposes a new gateway to the host by setting redirection. Introduction We explore how a gateway (a router) present in a LAN handles routing to the outside of this network and uses redirection to enhance this operation….
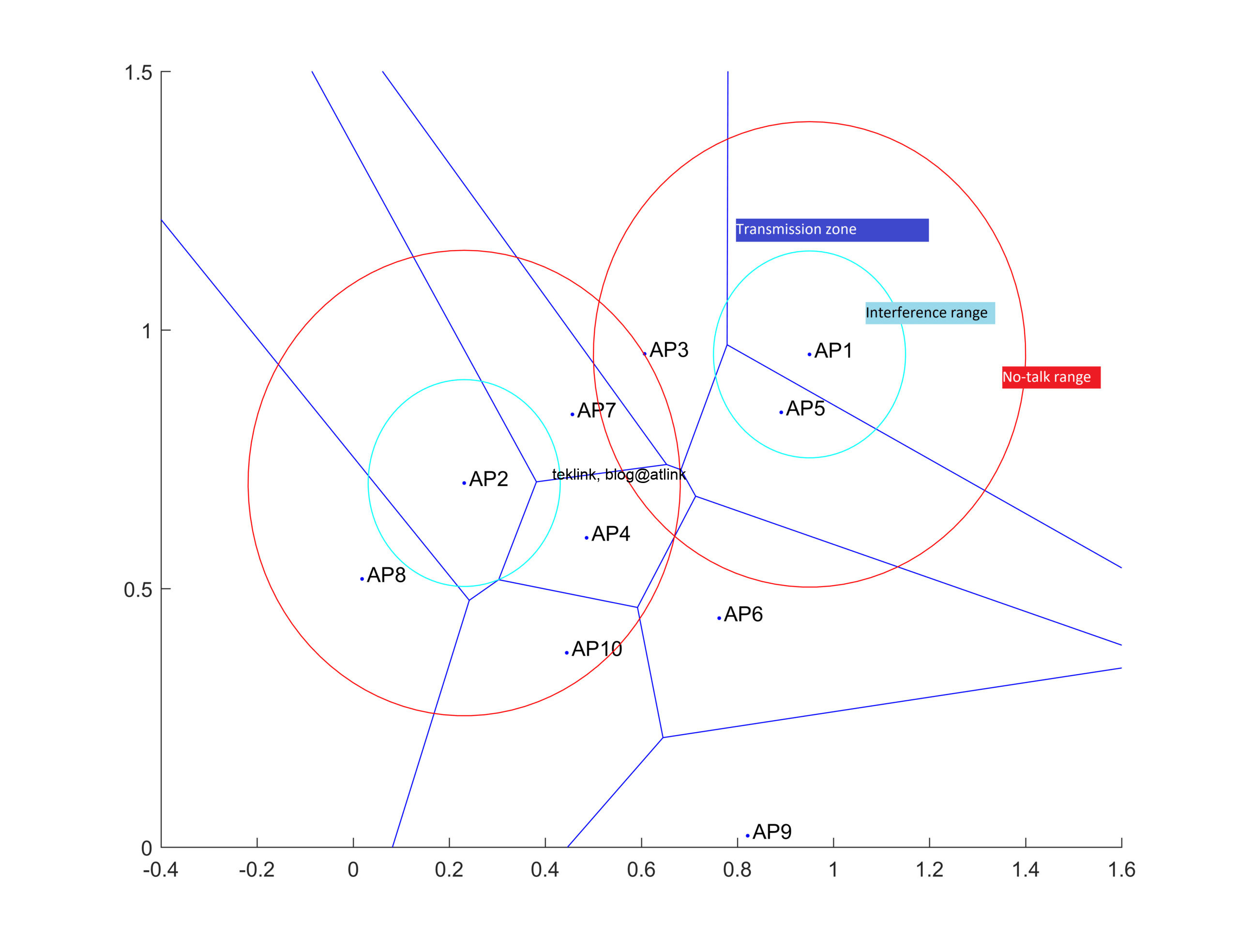
In this post, we present the work on radio coverage in Wlans, accessible at this address: A novel beamforming based model of coverage and transmission costing in IEEE 802.11 WLAN networks, about how to modalized the radio area coverage to enhance costing of the transmission opportunity in such networks. What this work is about The…...
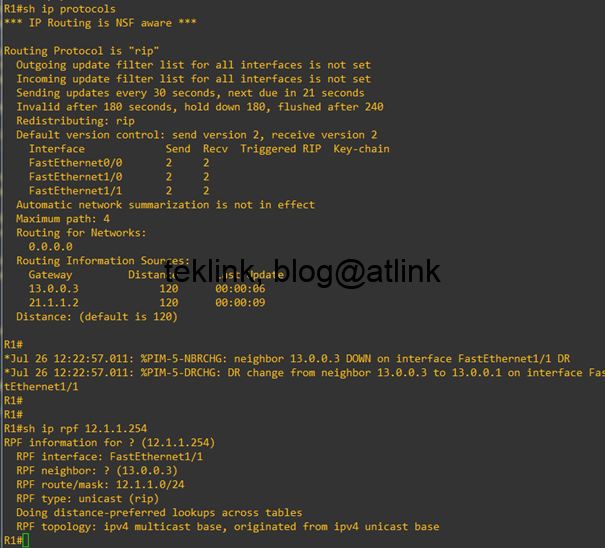
In this post, we work on our understading of the operation of RIP and how split horizon rule work Lab setup In our setup, R1 and R2 routers are in RIP domain and exchange information about loopback 0 and 1 networks. R1 is participating also to a static routing domain and advertises loopback 88 and…

In this post, we present the work accessible via this link: dRRMize your WIFI… and get your head out of the box!, about radio resources management in a WLAN enterprise network. RRM or Radio Resource Management being fundamental to the operation any unified wireless network and a master piece of any WLC (the Wlan controller)….
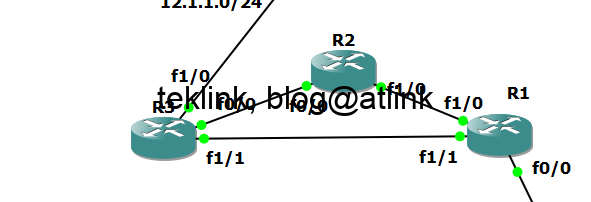
This post is a part of series of posts about RIP dynamic routing protocol. Here we deepen our understanding on how RIP protocol advertises learnt RIP routes. A simple case is where a route is in the middle of this update process dans got a better route than RIP. Introduction Let’s recall first that RIP…