A Novel Beamforming Based Model of Coverage and Transmission Costing in Ieee 802.11 Wlan Networks
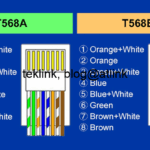
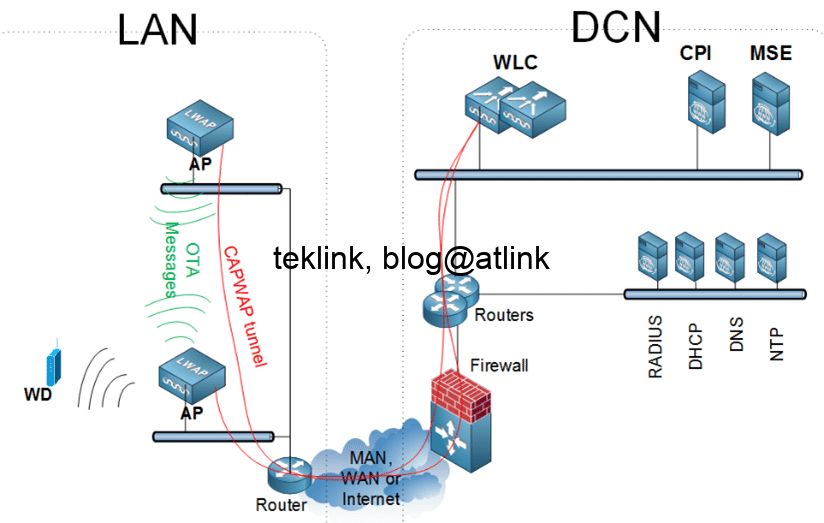
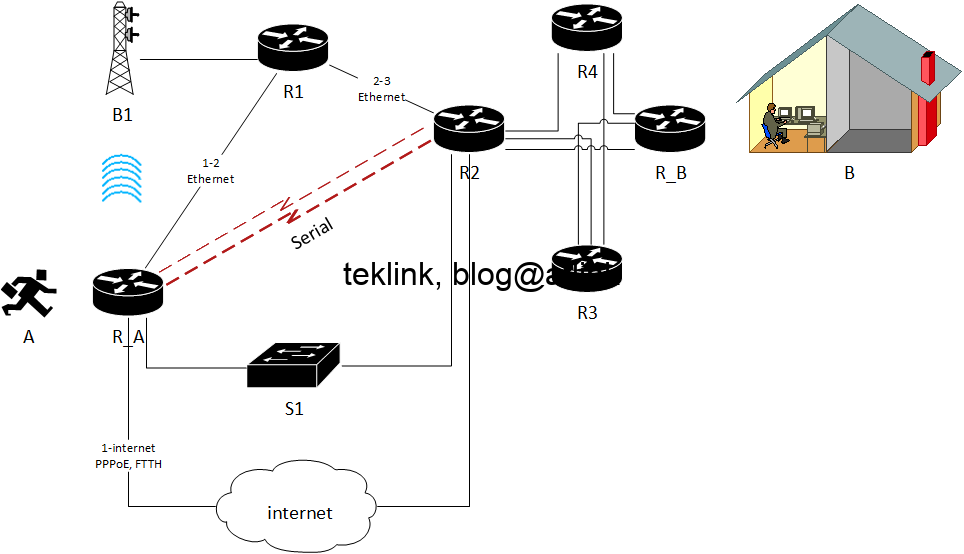
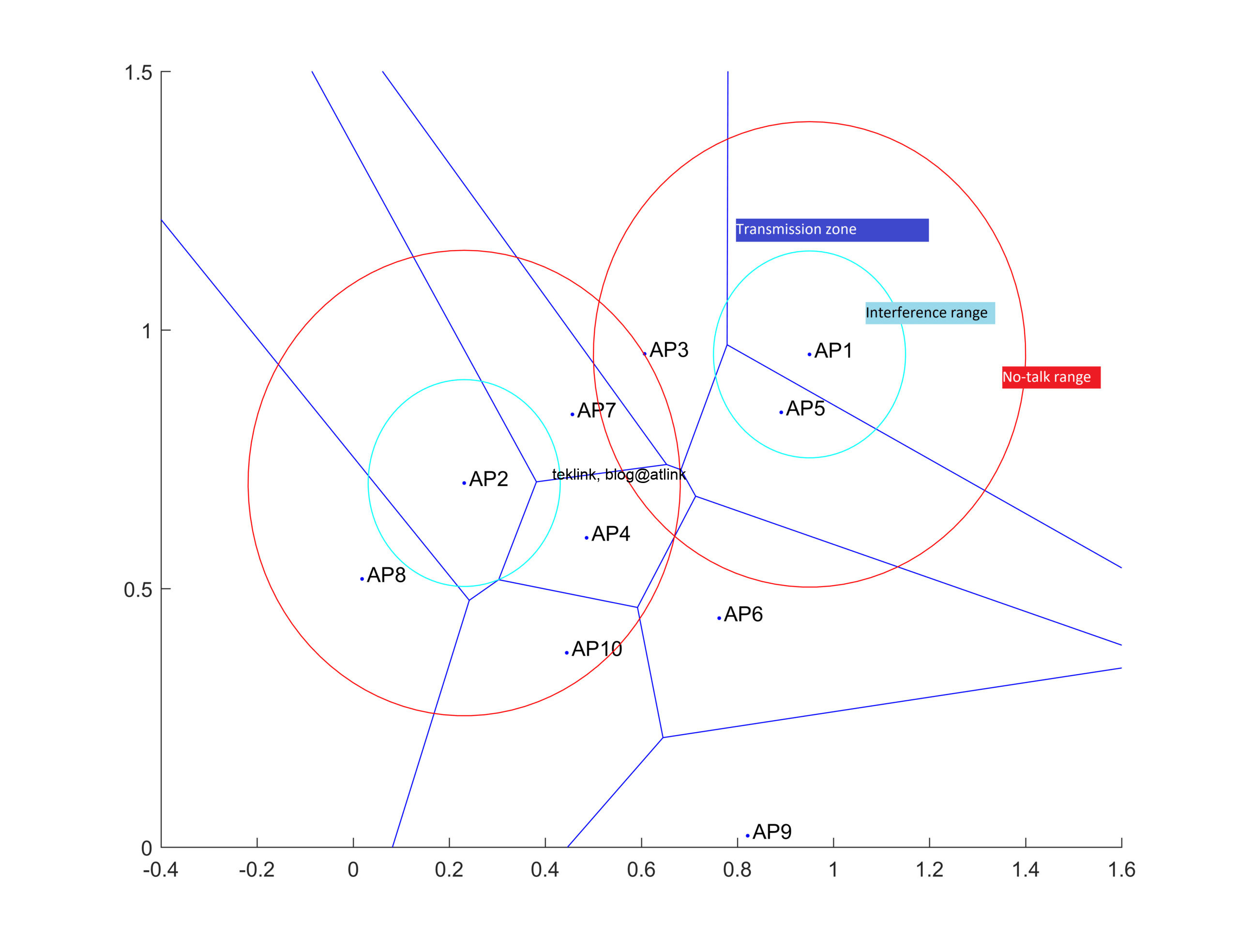
In this post, we present the work on radio coverage in Wlans, accessible at this address: A novel beamforming based model of coverage and transmission costing in IEEE 802.11 WLAN networks, about how to modalized the radio area coverage to enhance costing of the transmission opportunity in such networks. What this work is about The…...