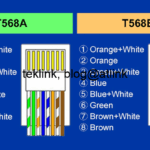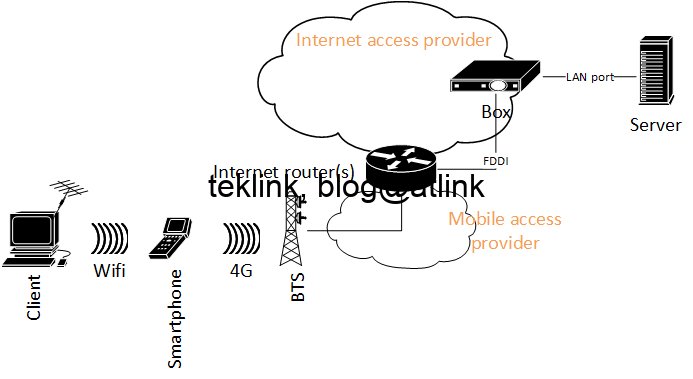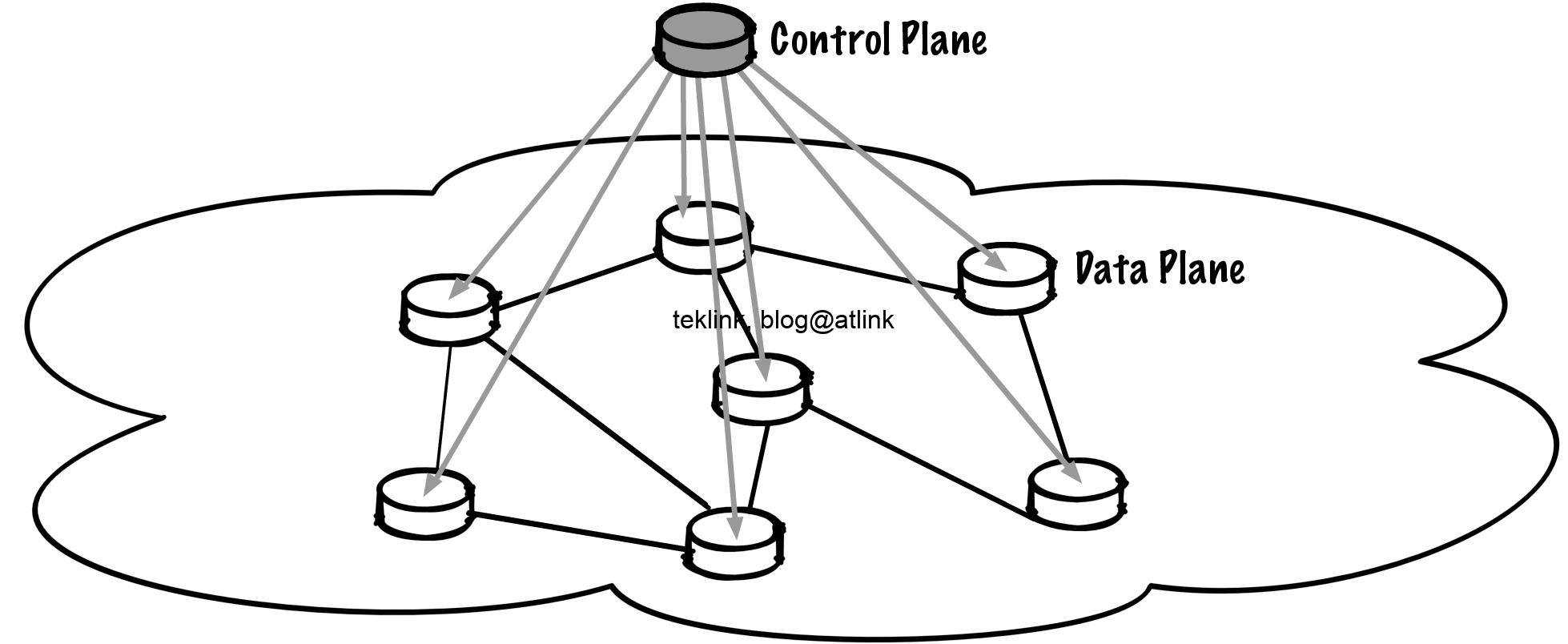
SD-WAN Big Picture!
Dans ce blog, nous discuterons du SD-WAN pour essayer de comprendre son enjeu et avantage pour l’entreprise. Nous commençons par explorer l’offre du marché, définir la technologie et son principe de base, du besoin de son usage et scénarios, avant de discuter de son architecture, implémentation et troubleshooting de son opération. Marché (offres du) Incontestablement…...