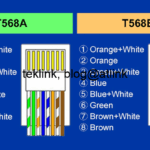
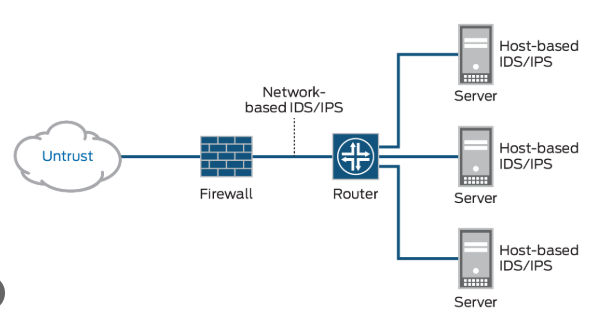
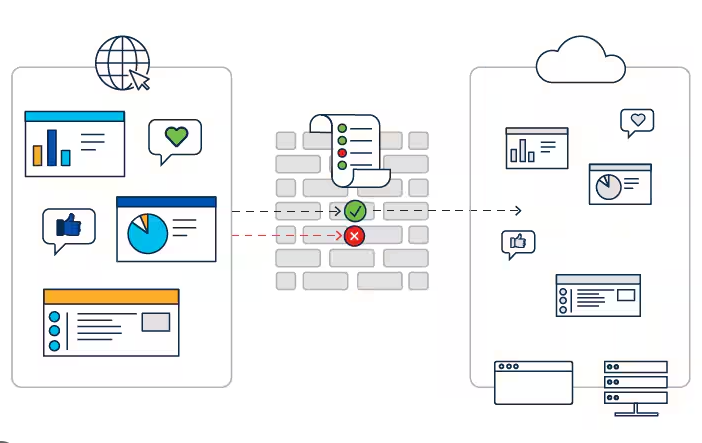
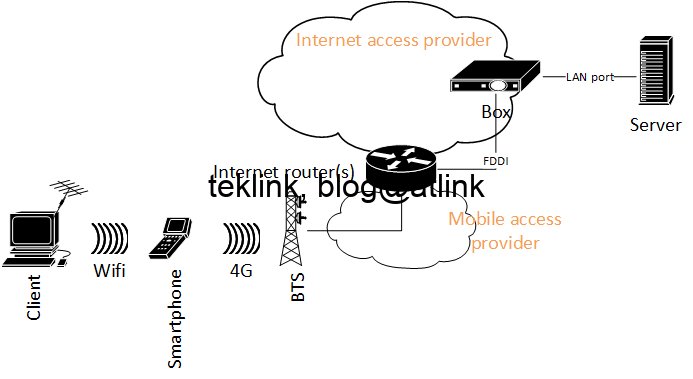
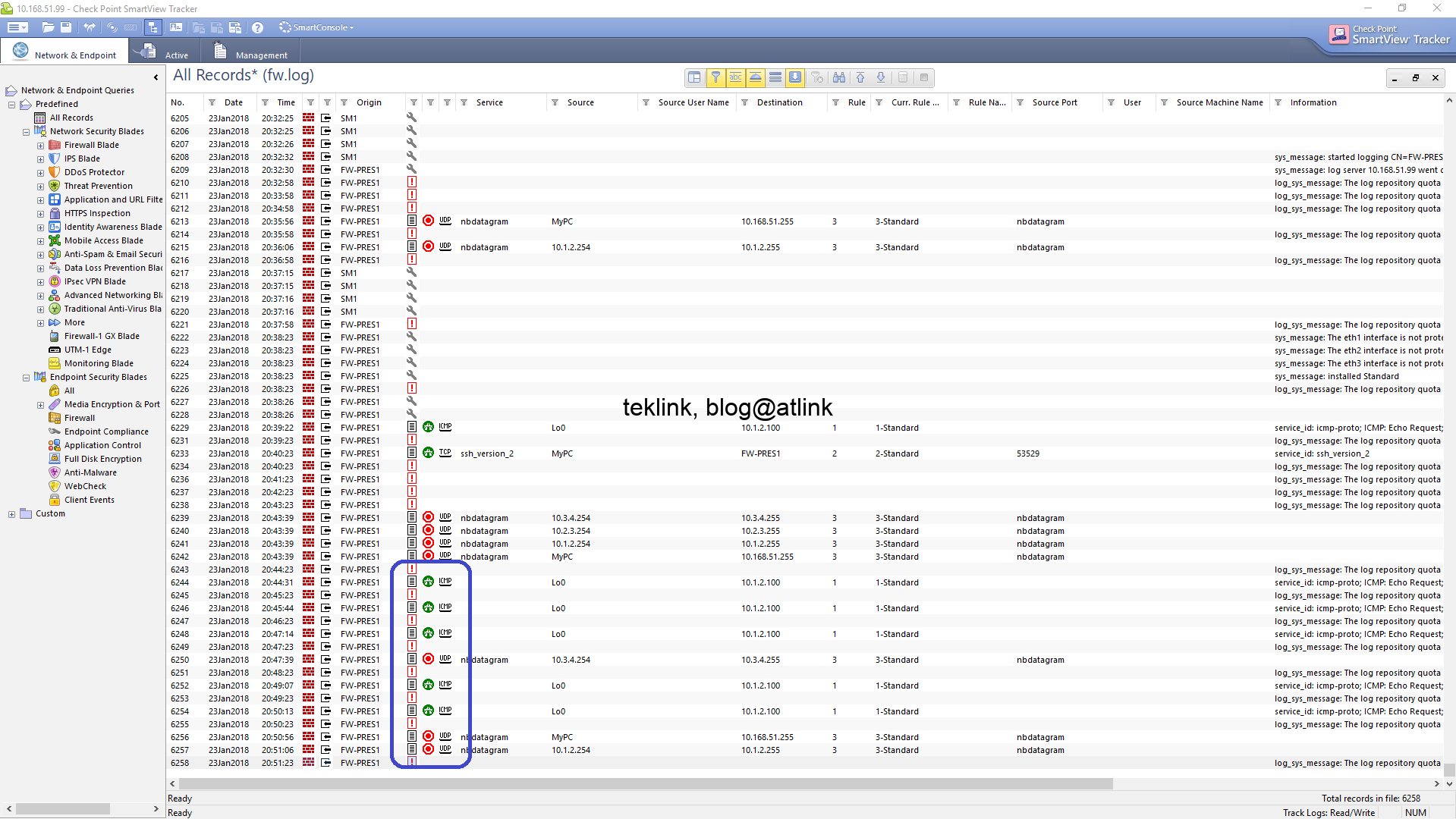
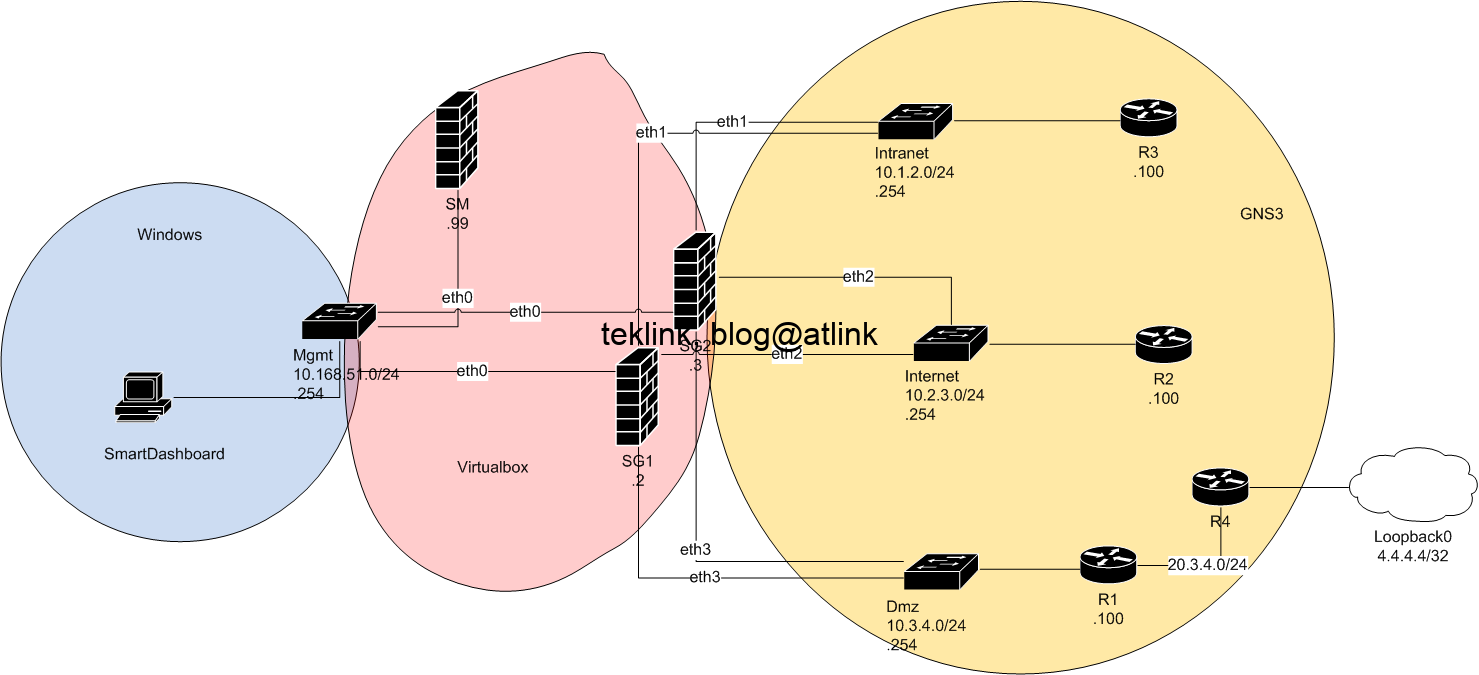
Secure a Home Network Like a Hack!
In this blog, let’s build a procedure, using open source tools, to secure like a cyber security professional an example of network, a home network, simple as that! Introduction Definitely, a home network like it sounds looks easy : a small router that gives access to internet with basic features, a local area network with…...