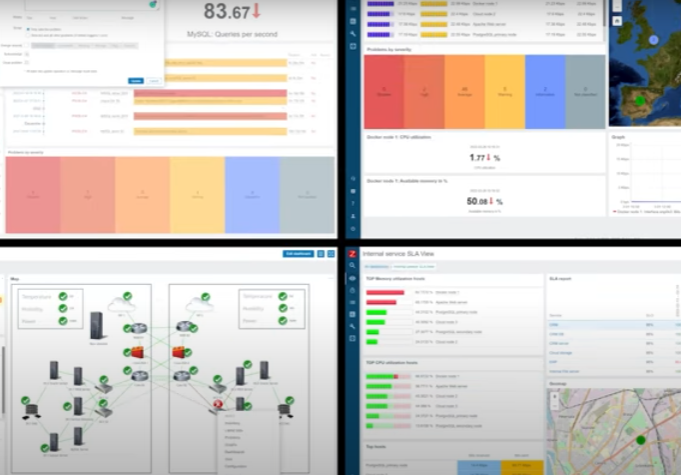
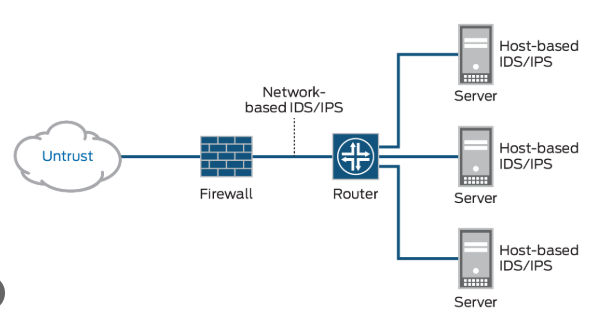
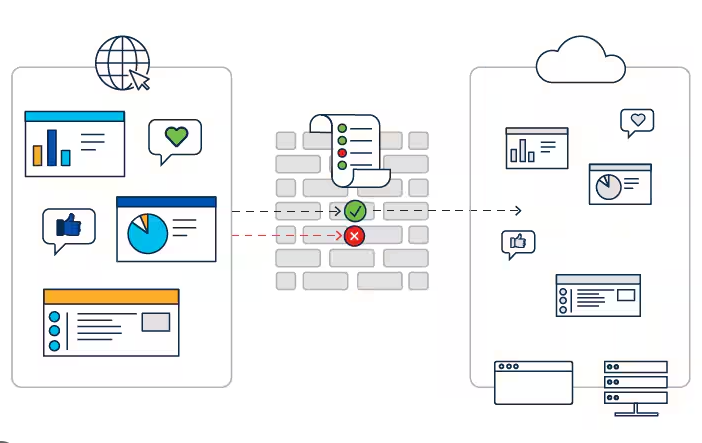
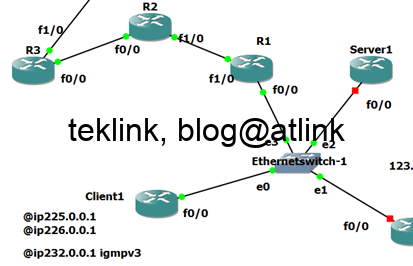
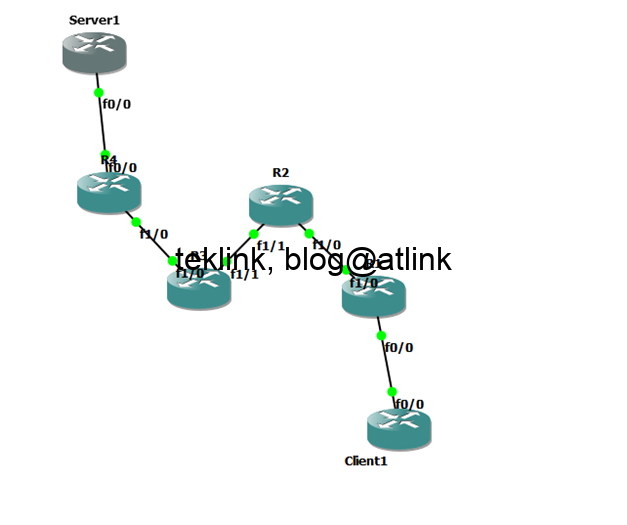
vPC Versus VSS Technology
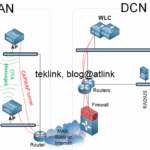
Dans ce blog, nous discutons vPV et VSS. Introduction Si l’objectif “historique” est le même : s’affranchir de la limitation de STP (blocage de ports pour prévenir les boucles), de l’usage des FHRP (HSRP, VRRP) pour équilibrer les liens, d’augmenter les performances en débit et capacité de calcul, d’éliminer les SPOF liés à l’utilisation d’un…...