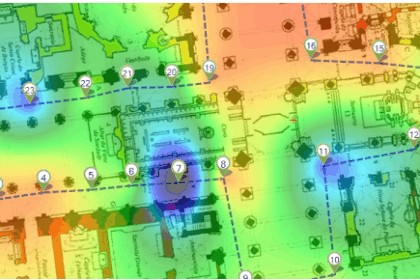
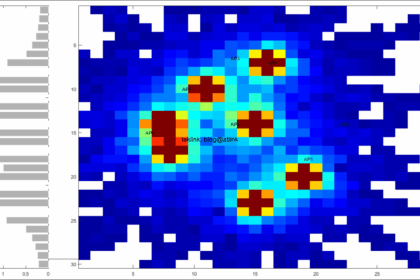
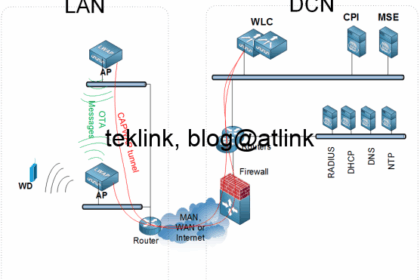
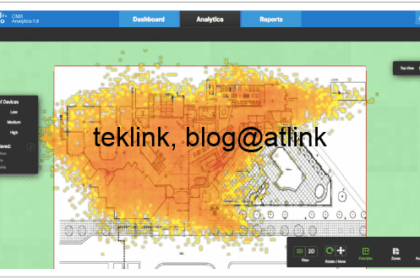
Presenting ARM In this post, that is a part of a serie of post that discuss how Wlan to radio ressources management, we talk of Aruba way of doing it. The figure shows a simple wlan network of 6 AP or...
In this blog, we discuss 10 security measures or controls that a LAN should have enabled. Introduction Before we present the 10 security measures to enable, let’s introduce the operation of a sw...
TPC stands for Transmit Power Control. It’s a one of Cisco RRM, Radio Resources Management, techniques that are aimed at tackling interference, cross and co-channel, in Wlan networks. RRM: TPC, C...
In this post we present our work on RRM solution and we present our proposed machine learning (ML) optimization to a general operation of dynamic RRM. Please contact us for any question or report dire...
There is no excerpt because this is a protected post....
Dynamic Radio Resource Management helps overcome interferences in dense WLAN deployments. By processing data from upper-layers services, it could optimize and enrich end-to-end wireless client experie...
Ansible (1) Aruba (1) Blockchain (2) Checkpoint (3) Cisco (32) Connectivity (38) Creativity (13) Cybersecurity (1) Extreme Networks (1) Fortinet (1) GNS3 (11) Linux (1) MachineLearning (1) Microsoft (4) Productivity (5) Python (1) RFC (1) Scapy (1) VirtualBox (1) Wireshark (7)
- Protected: An Example Network From Scratch… Internet AccessThis content is password protected.
- Protected: An Example Network from Scratch… Build the Wifi NetworkThis content is password protected.
- Protected: An Example Network From Scratch… On-Premise Network Automation With AnsibleThis content is password protected.
- Protected: An Example Network From Scratch… Build your Network SecurityThis content is password protected.
- Travailler Son CVLe CV est une étape importante de toute recherche d’emploi, au moins pour initier le processus (répondre à une offre, candidature spontanée, etc.)… plus encore, c’est une occasion de se poser, de réfléchir son développement, son expérience et de se projeter dans une nouvelle opportunité! Une approche classique du CV Pour nombre de “demandeurs d’emploi”,
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | |||
| 5 | 6 | 7 | 8 | 9 | 10 | 11 |
| 12 | 13 | 14 | 15 | 16 | 17 | 18 |
| 19 | 20 | 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 | 31 | |