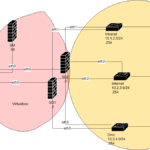
Next, on a windows 10 64-bit operating system we create 4 VirtualBox Host-Only Ethernet Adapters (loopbacks) that represent each a security zone such as in the figure:
These adapters correspond to the switches: Mgmt, Intranet, Internet and Dmz, in our topology. We configure them with the corresponding .254 ip addresses.
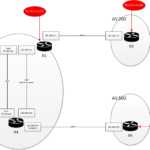
Map firewall interface to the correct network
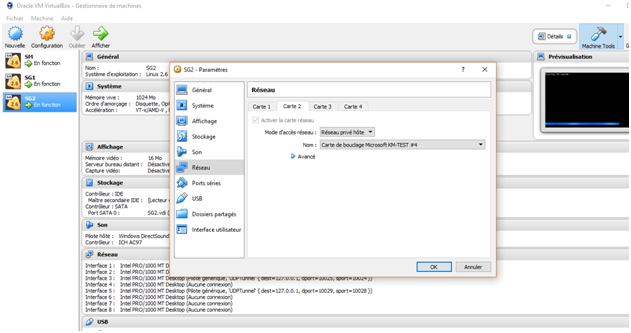
In VirtualBox we map each loopback (adapter) to the corresponding firewall physical interface: MGMT adapter to eth0, INTRANET to eth1, INTERNET to eth2 and DMZ to eth3. We do the same for both firewall. If we need to add another device interface in any of those zone subnet we just map them.
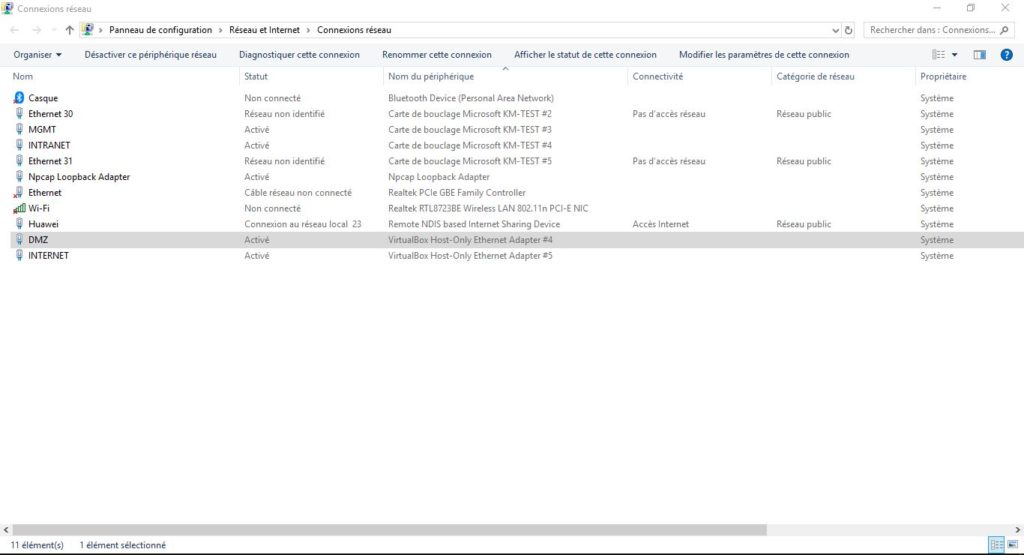
After the interfaces are mapped, the next step is to configure to IP for them to be able to communicate.
Security gateways and security manager need to be configured with the correct ip addresses in the management network from the console (CLI or command line) at initial install or using this command afterwards :

Some ping tests
At this stage we could check that all firewall are pingable from the corresponding consoles. On the management PC we install the Check Point management suite: Check_Point_SmartConsole_and_SmartDomain_Manager_R77.20_T124_Windows.exe.
Our SG gateways in the SM
We gain access to SM using SmartDashboard and add our security gateways. In this procedure SIC (that stands for Secure Internal Communication) is used to establish trust between gateways and security manager.
SIC procedure
At the gateway level, SIC is initiated in expert mode by cpconfig command. At the security manager level, SIC initialization is done using SmartDashboard as show in this figure: