What Is the Best Way of Subnetting?
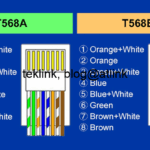
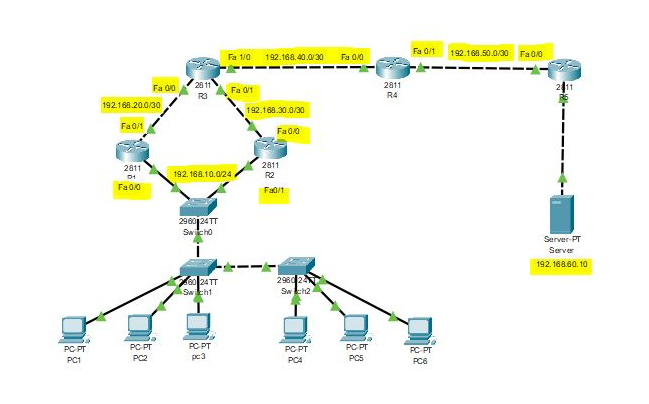
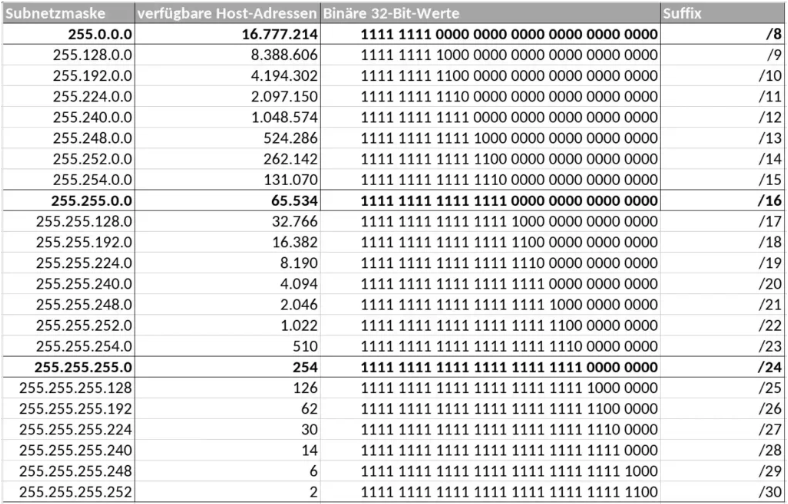
In this post, let’s recall what is subnetting for routing and switching purposes and how it is done. Motivation Network subnetting is very important subject that maybe referred to as VLSM for variable length subnetting. The basic idea is about managing a space of IP addresses (IPv4). Historically, a network length or space was fixed…...