Multicast Routing: A Step By Step… Part 1/6
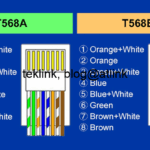
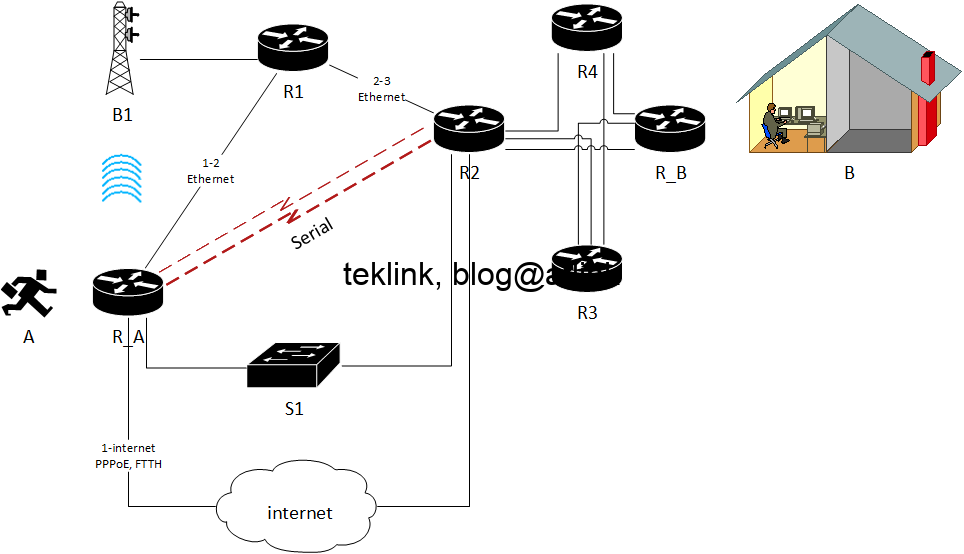
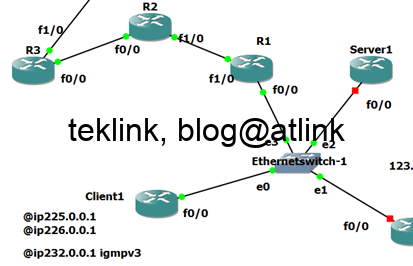
In this post we review a basic multicast routing operation, step by step using output from routers console and traffic packet capture (using wireshark). Introduction This blog is a part of a serie of blogs about multicast routing: How does multicast work In IPv4, multicasting servers use class D range of addresses: 224.0.0.0-239.255.255.255. Some addresses…...