
D.A.T(er) comme un Professionnel, un Architecte… et Ergonome!
Guide pratique de la réussite d’un Dossier d’Archiecture Technique ou DAT. Le lien vers le…

Guide pratique de la réussite d’un Dossier d’Archiecture Technique ou DAT. Le lien vers le travail complet est: D.A.T(er) comme un professionnel, un Architecte… et Ergonome! Au centre de cette activité, le DAT Le DAT s’inscrit en amont dans le processus de définition et réalisation d’une solution technique en réponse à une demande besoin. Il se…
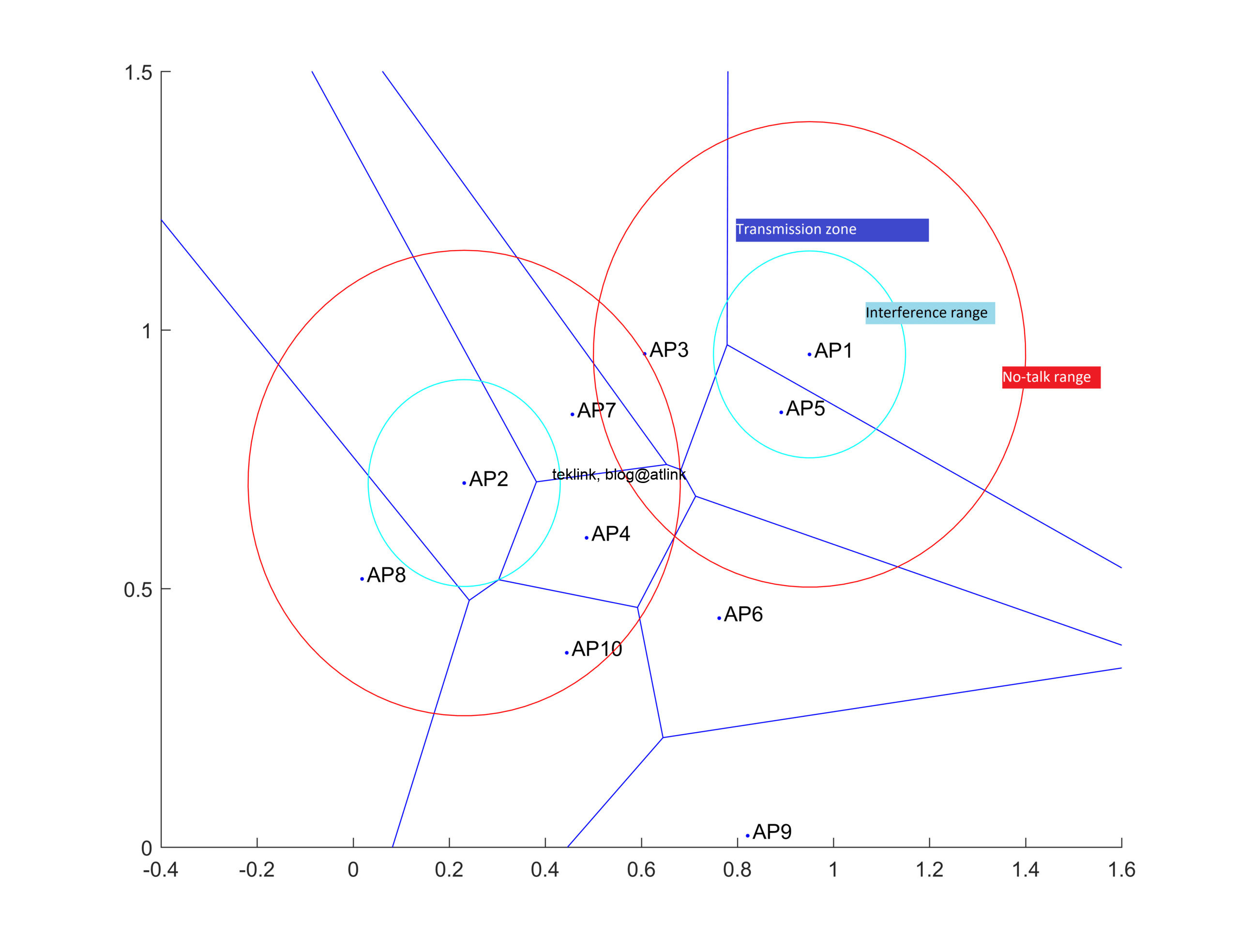
In this post, we present the work on radio coverage in Wlans, accessible at this address: A novel beamforming based model of coverage and transmission costing in IEEE 802.11 WLAN networks, about how to modalized the radio area coverage to enhance costing of the transmission opportunity in such networks. What this work is about The…...

Wireless technology is everywhere, overwhelming, in the heart of every IT architecture, and this is for many reasons: increase of user mobility, ease of network operation, scalability in deployment, enabling of localisation services, user and equipment presence detection, etc. A littre introduction It is a fact that the technology supports a wide range of applications…
In this blog’s, let’s discuss a “winning” strategy to start mining. Introduction First of all by definition mining is the technique by which you help build the blockchain. let’s imagine that the blockchain in this scheme is like a “big” distributed computer made of all miners computers. the central intelligence of this computer allows the…...

Qui de l’IA ou de la Créativité dicte sa volonté? sujet très passionnant et qui ne manquerait de vous intéresser. Mettez vos gants et en garde ! Au 1er round Indéniablement, la créativité est la forme d’activité humaine la plus complexe. Elle se mesure au génie humain (des érudits, savants, artistes, inspirés, les “ayant un…...
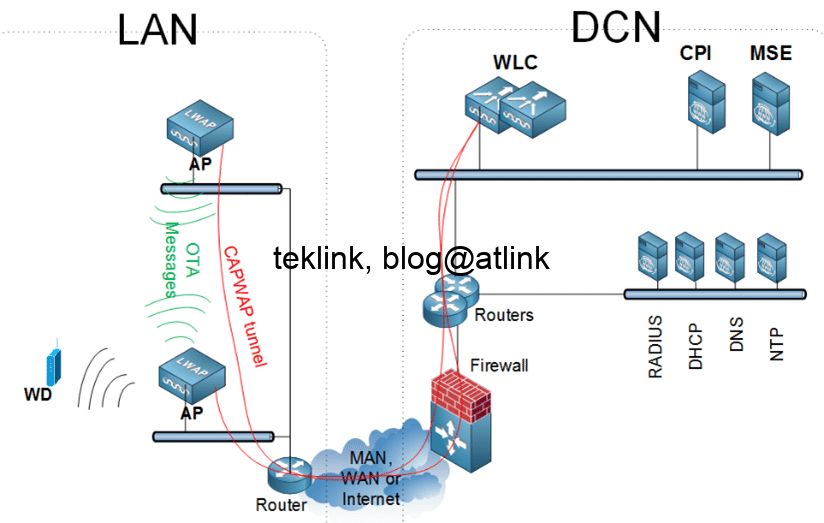
In this post, we’ll review the general idea behind NAT operation and how it could affect positively (friendly) or negatively (unfriendly) the performance of our network services on the cloud. Introduction Networks (and applications) are getting more and more global and the usage of NAT is inevitable. To run application efficiently such global networks (that…