Introduction
In this series of posts we’ll explore routing operation. Let’s start from the general idea of how could we manage traffic, a move from one location to another…
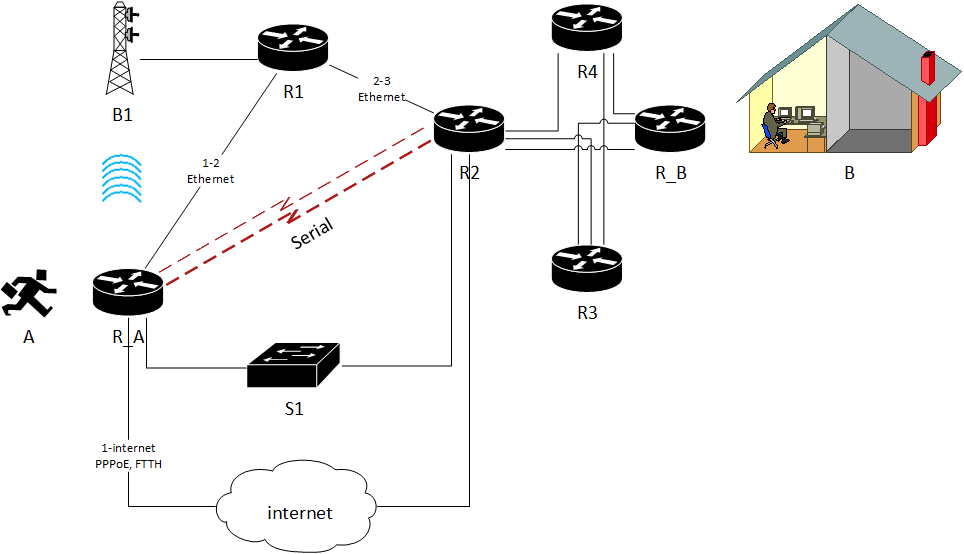
” This person needs to go back home at the evening! ” means that there’s a one way in return route to and from its office. We could have broadcast multicast or unicast it in one direction (unidirectionally) to get it from A to B if B is still unknown but we couldn’t afford lost him back home (now that we suppose we know about B and A precisely, uniquely)…
Should the one way and return route be the same? if not, then we talk about asymmetric routing. In some cases it’s advantageous to have asymmetric routing. In others, where firewalls per example, are put into play, symmetric routing is more appropriate (return packets should use the established session opening sat up by the initial packets). In asymmetric routing, what is asymmetric? the processing of packets… But if the return packets flow the same way but in the opposite direction, we talk about symmetric routing.
Is it necessary… routing?
Is routing necessary for person A?
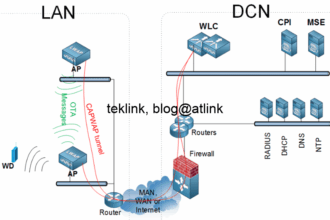
Yes, in packet switched network, it is necessary to show person A what route to follow at each node (router), in the network. Home and office networks are different and far away from each other: we need some kind of inter-networking to allow them communicate. When A reaches router R_A, it brings information about B, this information should be sufficient to move A to the next step (router). In our example we’re presented by 4 choices to reach R2. At R2, A present the same information about B to router R2. Because the routing decision is consistent in the this network, R2 would froward A towards R_B.
No, routing is not necessary if we use LL leased line: modem, v.24, 35 or X.21 interface type to connect person A to B. Other switched circuits technologies such as: Frame Relay (FR), X.21, ATM, P1024B or C, would serve the same purpose. More advanced technologies would help also avoid routing: tunnel, vpn, vrf, xconnect, vpls, pseudo wire, mp-bgp, mpls labelling, etc. In this cas, we’re sur that the “tunnel” will conduct A directly to R_B; there’s no other possible choice or chance of a routing mistake…
Where to use routing?
If yes, then where? in the above described transport network?
At any router level, if it’s not L2 (doing bridging, etc.). But per definition, in OSI, a router is by default, if it’s not differently specified, a L3 device.
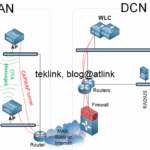
In the internet (as shown in the figure), the routing is not done by our help but requires other guys, ISP, to do it for us.
At any switch, if the switch is L3. But if it is not specified, a switch is by default, following the standard, a L2 device…
An alternative to routing
If not, what are some of technologies, protocols, or strategies to achieve the same? without routing?
“without routing” means no router in between A and B. In other terms, a traceroute (for example) from router A to router B, would show only one hop to reach person B.
Technologies maybe reordered following the OSI model from top (requirement underlay) to down:
- tunnel, vpn: vrf, xconnect, vpls, pseudo-wire, mp-bgp, mpls, lables, etc.
- switched circuits: frame relay, atm, x.25, fixed or on-demand switched circuits, dial-up, adsl, etc.
- leased lines: modem, analogic, numeric, low rate, v24, v35, x21, interfaces, etc.
Routing possibilities
If routing is put in place, what are our possibilities? the maximum number of possible routes? that you can offer Mr. A to join Mr.B?
The total number of possibilities, without any selection, is roughly equal to the possibilities at every routing node…
Are all the possibilities logical, make sense? what do you think of A going through router R1 and then looping back to R_A? in cases where routing is done based on the packet destination address, source address, or both?
In the case of destination-based routing, a minimum criterion is that any possibility should help lead person A to B. We wont accept routes that loops back, leads to the same departure, “cycles”…
What types of loops would you imagine in general? loops maybe of many levels: L1, L2, L3, at processes level, mental, intellectual, etc.
- L1: frequency synchronisation in DWDM is a good example of such loops if lower stratum number get updates from higher stratum in some way. No way to troubleshoot…
- L2: STP spanning tree protocol in LAN network, (ieee 802.3d, rstp, pvst, pvst+, mstp, etc.), if there are redundant physical links and no stp is active or buggy… another way to prevent from such loops: TRILL, fabric path, ring vendor topologies (such as Extreme Network ESRP protocol), etc.
- L3: routing, bad routing decition that breaks routing per definition or its performance…
- Process: with regards to some task, working but able to move forward or get new results, building and destructing continually, etc.
A loop is a symbol of a misuse, of disturbance, bad choice or decision…
Based on the “loop” criterion, the total number of possibilities is 25 in our network!