D.A.T(er) comme un Professionnel, un Architecte… et Ergonome!
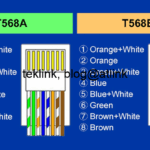
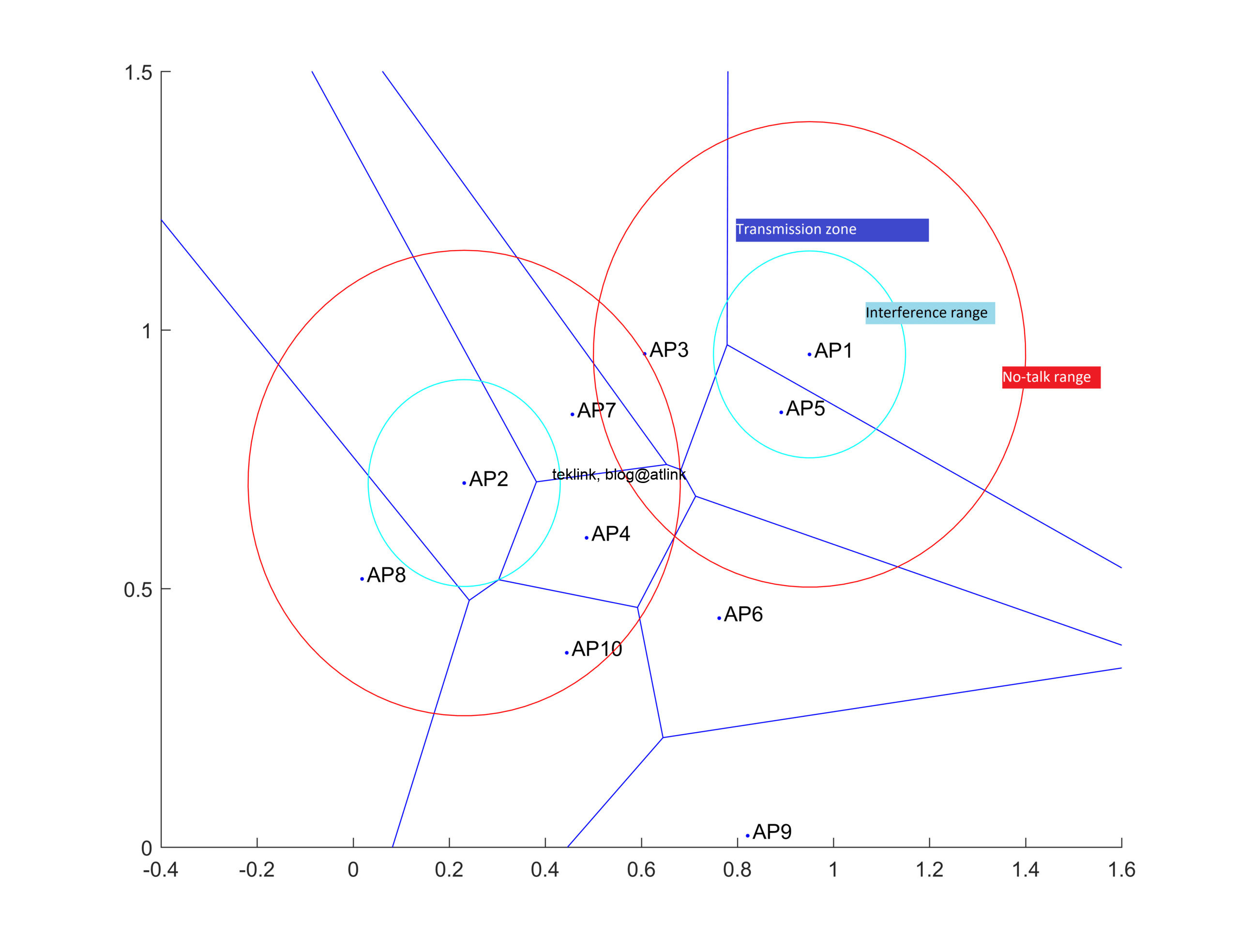
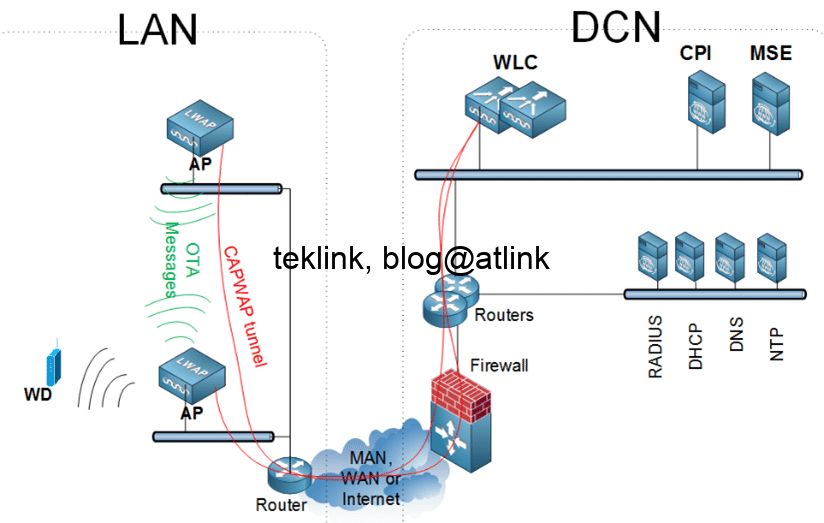
Guide pratique de la réussite d’un Dossier d’Archiecture Technique ou DAT. Le lien vers le travail complet est: D.A.T(er) comme un professionnel, un Architecte… et Ergonome! Au centre de cette activité, le DAT Le DAT s’inscrit en amont dans le processus de définition et réalisation d’une solution technique en réponse à une demande besoin. Il se…