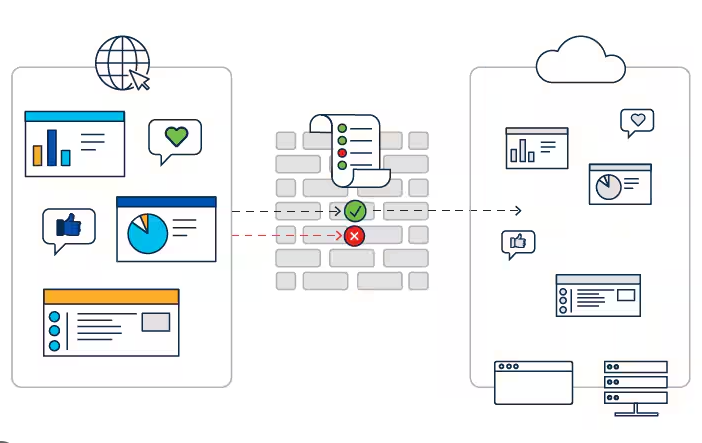
In this blog, we discuss 10 security measures or controls that a LAN should have enabled.
Introduction
Before we present the 10 security measures to enable, let’s introduce the operation of a switch in a LAN network.

Switches
An Ethernet switch is the central element of a LAN network and operates at data link OSI layer. Every switch port defines a collision domain and can extend a broadcast or broadcast frame domain that is stopped by a router routed interface that operates at network OSI layer.
Broadcast domain
By default switches support one broadcast domain that can be tight to the default VLAN. VLANs, Virtual LANs, allow extension of this number to no more than the reserved 12-bit coded in the IEEE 802.1q frame header. This number depends on other design and technology considerations: VTP deployment, reserved VLANs, etc. Two types of links: ACCESS and TRUNKS, are used to interconnect LAN network elements: stations, servers, routers, switches, etc. Access ports could not be tight to more that one Vlan. Trunk ports supports number of Vlans over the same physical attachment.
Switching
Switches help get more network capacity and minimize frames switching delays. Switching is done at hardware level for unicast and known addresses frames. For other traffic: unknown destinations unicast, broadcast or multicast, switching may be handled at processor level. To help switching track destinations MAC addresses, a Content Addressable Memory, CAM table is built. This table matches MAC addresses to traffic source switch ports.
You notice that switches operation is very sensitive to whole network operation and services. It needs to be secured to conform to global security policy. Next we explore 10 risks that may challenge our network and 10 security measures to overcome them.
Risks
Risk may concern CAM maintenance, ARP, DHCP, STP or IP protocols operation:
MAC poisoning,
is when CAM table is filled with invalid information making it impossible for return traffic to reach legitimate destinations. This mechanism could be used to simulate MiM attacks or to overflow a target with unwanted traffic.
MAC flapping,
here source MAC flaps over many switch ports. If the same MAC address appears on another port that the one behind the legitimate source of traffic, switch may forward return traffic frames to the wrong destination or treat them at processor level which may be resource consuming. Frequency of MAC flapping may impact re writes of CAM entries, frames switching delays, etc.
A short comparison of this attack to the first one is based on the frequency of CAM entry changes: the impact on traffic is partial as a part of it is still processed at hardware level, another part is being sent to wrong destinations, and the last part sent to all switch ports.
MAC overflow
is aimed at over filling CAM table making it impossible for legitimate sources to hardcode their MACs at CAM level. Their traffic is then treated at processor level as if it was destined to unknown destination and flooded to all switch ports. This process is very resource consuming in case of huge traffic and may impact control plane operation and connected hosts.
The majority of clients connected to LAN implement TCP/IP stack and make use of DHCP to get IP addresses dynamically and necessary information to access network services. We explore next, risks related to the operation of this network service:
DHCP rogue server
in this attack a pirate DCHP server distributes IP addresses and network information to network clients. To access outside network victims may be hinted to use a pirate gateway instead of the legitimate one. Other services vulnerabilities may be exploited: DNS, DHCP options, etc. It’s a kind of MiM attacks.
DHCP rogue client
in this attacks addressable DHCP space is exhausted by rogue DHCP clients preventing legitimate clients from having an IP address and access to network services. It’s an example of DoS attack.
IP clients need IP addresses to forward their packets. In addition, they need locally the corresponding destination MAC address to forward frame at layer 2 and reach remote destination. ARP is a layer 2 protocol aimed at IP Address Resolution to MAC for switching purposes in Ethernet LAN network. Some attacks could target this service:
ARP poisoning
The objective here is to correspond an IP address to a fake MAC address hinting the sending part to send traffic to a wrong gateway or destination. Gratuitous ARP mechanism is commonly used for this purpose.
ARP overflow
the objective here is to exhaust the ARP table or cache capacity preventing hosts, servers or network nodes from storing previously ARP resolution results. For every packet to be transmitted a new resolution must be triggered and responded to which increases control traffic, number of packet drops, and processor resources.
ARP spoofing
the attacker here alters the content of the ARP packet itself: IP or MAC information. It intercepts and uses reply and request packets instead of gratuitous ARP mechanism for this purpose.
Other attacks may focus on the IP packet itself or by exploiting vulnerabilities of certain layer 2 protocols:
IP spoofing
this is a good example of a Distributed Denial of Service, DDoS attack, where an attacker spoofs source IP information so that return traffic points to a victim. Then all destinations unexpected return traffic is targeted at this victim address causing a denial of service.
Storms
these attacks are aimed at overloading network with normal and exception traffic. They exploit layer 2 protocols such as STP misconfigurations, system bugs, etc.
As a wrap up
Switches are central devices in any network to secure their operation many strategies can be put into place against attacks such as : mac poisoning, flapping or overflow, dhcp rogue client or server, arp poisoning or spoofing, ip spoofing and finally storms…
In the upcoming blogs, we’ll discuss other securing aspect of the network operation.